You probably heard about ingesting group policies with Microsoft Intune, or Windows CSP. If not this is a great way to extend the ordinary Intune settings with thousands more settings, just the ordinary group policy settings.
There are a lot of great reading on this subject, including Microsoft documentation
Understanding ADMX-backed policies
Win32 and Desktop Bridge app policy configuration
Policy CSP, Configuration Service Provider
In this article we will utilize this way to configure OneDrive KFM, Known Folder Move and other OneDrive settings like a pro and without scripting.
Why without scripting? I have seen so many times scripts that nobody “knows” how it works, they are not comfortable with changing it since the guy who wrote it is on vacation for 4 months, and many other reasons for not changing a script. The scripts should not be static. When group policy preferences was released to Windows this was a huge benefit, scripts could be at a minimum and the documentation got a lot better, in general people could understand what happens a lot easier.
So now is the time to do the same with Intune and Policy CSP and ingesting ADMX! And actually get some status back, if the setting was set correctly or not.
(don’t get me wrong, I love scripting but that should be used were it fits best, not just as the first choice)
First note that I recommend running OneDrive version 18.171.0823.0001 with this settings, and if you are running Autopilot with Intune then you are not certain what version is on the machine, so I usually run PowerShell script to force a OneDrive update asap.
Ok, lets get to it.
First make sure you have a refence machine with an updated OneDrive agent, browse to the folder
%localappdata%\Microsoft\OneDrive and then latest OneDrive version and ADM. In my case this is the full path
%localappdata%\Microsoft\OneDrive\18.192.0920.0012\adm
First copy OneDrive.admx to %WinDir%\PolicyDefinitions and OneDrive.adml to %WinDir%\PolicyDefinitions\en-us (or your language folder of choice)
Then open the OneDrive.admx file in Notepad, and copy all the content. We need this content to ingest/install the ADMX file on the target machine.
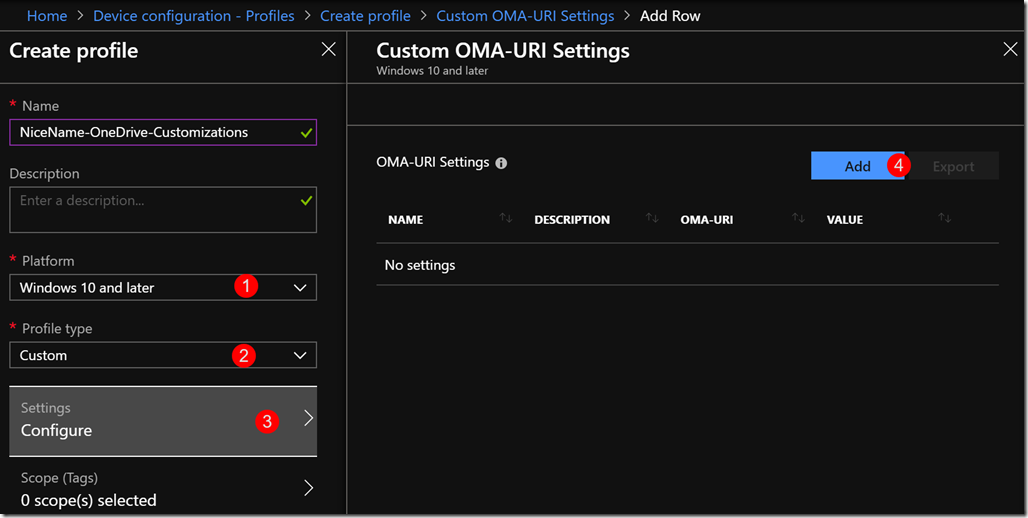
Create the Ingest OMA-URI by heading over to Microsoft 365 portal, https://devicemanagement.microsoft.com
Create a new Device Configuration Profile, choose Profile type Custom and press Configure, and press Add
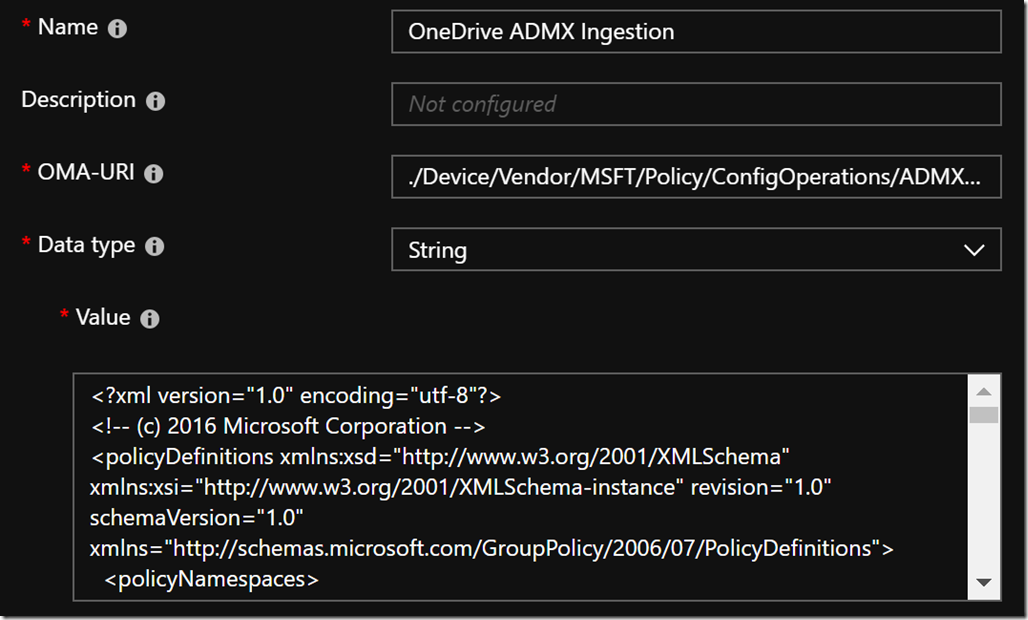
Name: OneDrive ADMX Ingestion
OMA-URI: ./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/OneDrive/Policy/OneDriveAdmx
Data type: String
Value: <paste the content from OneDrive.admx>
Now time to create some settings, if you know what to configure this one is easy (I will not do a deep dive here).
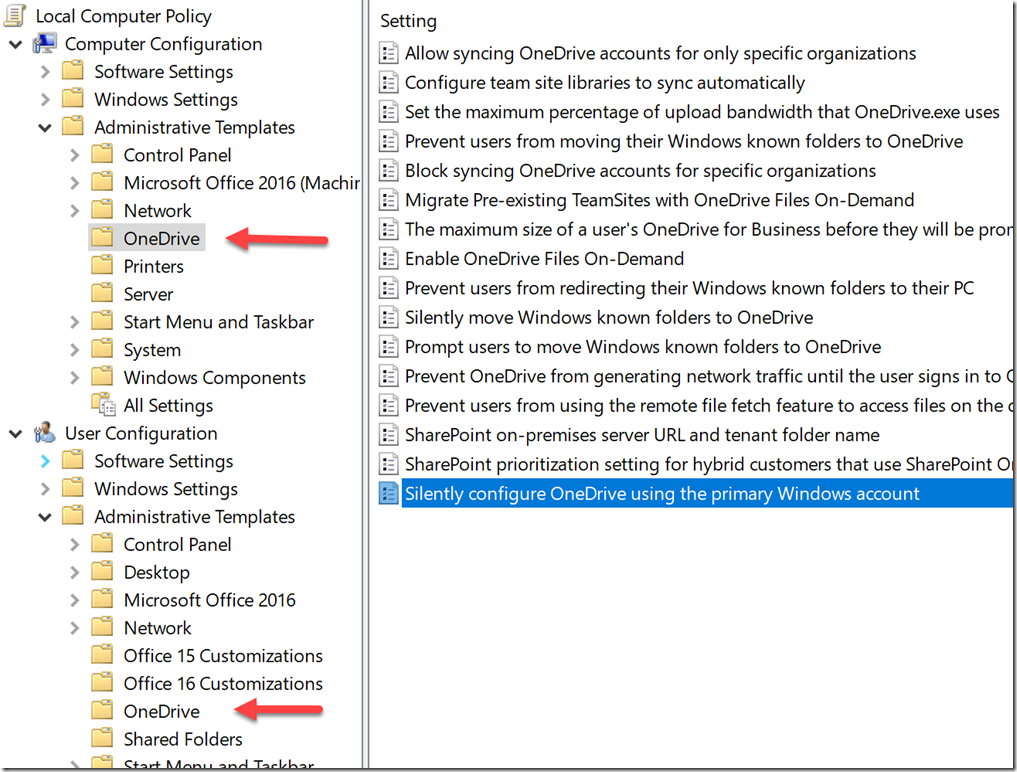
It will make it easier if you open gpedit.msc on your refence machine, and head over to the OneDrive settings, to understand what settings you’d like to set.
I have choose the following settings, most of these settings are simple Enable/Disable policies and is easily understood, some need a little more explanation. Also note some of the settings are User and some Device settings.
Prevent users from synchronizing personal OneDrive accounts
Name: Disable Personal Sync
OMA-URI: ./User/Vendor/MSFT/Policy/Config/OneDrive~Policy~OneDriveNGSC/DisablePersonalSync
Data type: String
Value: <enabled/>
Silently configure OneDrive using the primary Windows account
Name: SilentAccountConfig
OMA-URI: ./Device/Vendor/MSFT/Policy/Config/OneDrive~Policy~OneDriveNGSC/SilentAccountConfig
Data type: String
Value: <enabed/>
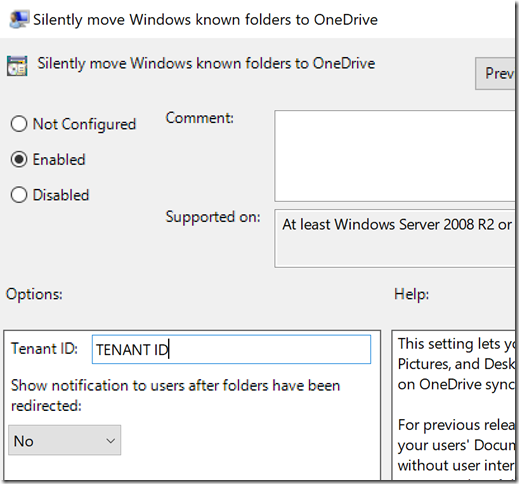
Silently move Windows known folders to OneDrive
Name: KFMOptInNoWizard
OMA-URI: ./Device/Vendor/MSFT/Policy/Config/OneDrive~Policy~OneDriveNGSC/KFMOptInNoWizard
Data type: String
Value: <enabled/>
<data id=”KFMOptInNoWizard_TextBox” value=”TENANT ID”/>
<data id=”KFMOptInNoWizard_Dropdown” value=”1″/>
Since this setting have more options, we need to enter them as well. So you have to know your tenant ID (You can find this in the Microsoft 365 portal > Azure Active Directory > Properties and Directory ID)
And you have to choose if you want notification or not for users (No = 0, Yes = 1)
Prevent users from changing the location of their OneDrive folder
Name: DisableCustomRoot
OMA-URI: ./User/Vendor/MSFT/Policy/Config/OneDrive~Policy~OneDriveNGSC/DisableCustomRoot
Data type: String
Value: <enabled/>
<data id=”DisableCustomRootList” value=”TENANT ID1″/>

Since this setting have more options, we need to enter them as well. So you have to know your tenant ID (You can find this in the Microsoft 365 portal > Azure Active Directory > Properties and Directory ID)
And you have to enter 1 for turning on the setting for that tenant id.

Prevent users from redirecting their Windows known folders to their PC
Name: KFMBlockOptOut
OMA-URI: ./Device/Vendor/MSFT/Policy/Config/OneDrive~Policy~OneDriveNGSC/KFMBlockOptOut
Data type: String
Value: <enabled/>
Have fun ingesting with OneDrive! Reach out to me if I missed anything!

Leave a comment