Everyone, Thanks for answering the poll in previous post! Most of you uses Active Directory to backup recovery information – I hope this post can help you to understand what you need to consider, validate and develop in the future.
With the release of Windows 10 1607 and 1703, there have been changes how to store the TPM password in registry, especially with Windows 10 1703. A part from that I have noticed there are confusions about TPM owner password and BitLocker recovery password and what each does and what is it used for. With the latest release this have just been more important to understand and make choices, I will try to explain and guide you to a choice.
TPM Chip?
First we need to know what a TPM chip is, it is a security device that is either a standalone component (discrete), dedicated hardware integrated into other components (integrated) or firmware based running in a trusted execution mode in i.e. CPU (firmware). This chip can store certificate, secrets or a state (i.e. BitLocker with TPM protection).
TPM exists in to versions 1.2 and 2.0, there are some major differences here apart from looking at hardware level such as algorithms, crypto etc. but if you have TPM 1.2 chip in your computer they can (and will) act differently from model to model and from vendor to vendor. There were no good standardization and when I say act differently I mean some models (and even Bios version) may show a physical presence notification and some not, also when you “hack” or enter wrong BitLocker PIN/Virtual Smartcard PIN/Windows Hello for Business information too may times the vendor defines how many times and for how long the TPM will be in locked state. Contact your vendor if you have questions about this.
With TPM 2.0 there is a standard, and that will be set when Windows 10 is taking ownership and managing your TPM. You have 32 tries, and every time you enter wrong PIN a counter will increate by 1 and that will last for 2 hours. So if you enter wrong PIN 1 time you have 31 tries left, and after 2 hours you will have 32 tries again (based that the device is turned on for 2 hours). What happens if you enter wrong PIN 32 times? The TPM will be locked for 32 x 2 hours = 64 hours, but after 2 hours you will have 1 try. The lock-out will not be per-user, but per-system, there is no way to differentiate users.

SO that was the long story, the short story: I like to see the TPM as a safe, a safe were you put things that you want to be securely stored such as password, PINs and states.
TPM 1.2 is nice to have, but TPM 2.0 is far better both in security and management.
For more information regarding TPM have look at this Microsoft documentation
TPM owner password?
The TPM owner password or authorization password is a complex password and is set when Windows boots for the first time and takes ownership of the TPM chip. The TPM can only be owned by Windows from now on and the TPM owner password is not possible in anyway to read. With a current valid TPM owner password it is possible to change the TPM owner password and unlock the TPM, but remember if you enter wrong TPM owner password the TPM will block those commands for 24 hours – so you will only have 1 try per day. It is not possible in any way to unblock the TPM with out a current valid password, so what if the password is unknown? Then you need to clear the TPM, that means BitLocker state information, Windows Hello information, Virtual Smart Card certificates etc. are discarded, deleted and unrecoverable, you need to reinitiate/reenroll that information. To clear the TPM you either use the PowerShell (Clear-TPM) or TPM.msc.
To unblock TPM or verify that you have a valid TPM owner password use PowerShell Unblock-Tpm -OwnerAuthorization “TPM owner password”.
Ok, but is it necessary to save the TPM owner password? Depending upon your requirements I would say – Do you need a way to unblock the TPM from “hacking” or too many invalid BitLocker or Windows PIN attempts?
If your answer to that question is Yes – you need a secure place to store the TPM owner password. So how do you store the TPM owner password then? Earlier there was a permanent way to store the TPM owner password in the registry but based on security requirements this have recently been removed and the password will only be stored temporary. Earlier there also was a way to store the TPM owner password in Active Directory, this have also been removed in Windows 10 1703. The only way to store the password is to either use MBAM, Microsoft BitLocker Administration, or a custom developed solution.
If your answer to the question is No – then don’t care about it. If the TPM have been blocked, clear it or wait 2 hours for next attempt. No management tools needed for this.
BitLocker recovery password?
So what is the recovery password? Lets go back to basic, BitLocker is hard drive encryption. It is possible to encrypt operating system drives, external and internal data drives. The encryption is locked/secured with one or more “protectors”, the protector can be a password, TPM, TPM + startup Pin, USB key, SID, numeric password… Windows 10 have 4 different options of encryption methods XTS-AES 128/256 or AES128/256, AES 128/256 with diffuser are deprecated.
The most common implementation of BitLocker is with TPM (depending on your security requirements with or without startup PIN), if you are us0ing ConfigMgr or MDT there are built-in actions for this.
How does the TPM (without PIN) protector work? In the simplest of forms I usually explain this as a set of “switches” (PCR) that is locked to a state when the computer is shutting down. A “switch” or PCR can be Bios settings, system settings, critical boot files, MBR etc. For a full list have look at the group policy setting Computer Configuration\Administrative Templates\Windows Components\BitLocker Drive Encryption\Operating System Drives\Configure TPM platform validation profile for BIOS-based firmware configurations or Configure TPM platform validation profile for native UEFI firmware configurations while looking at the setting, also have a look at the default settings to get an idea of what BitLocker can be trigged upon.
So when the computer boots the state is compared and if there are one or more “switches” that doesn’t match up the BitLocker will ask for a recovery password.
Possible reasons for the BitLocker recovery password question to appear I would guess are
- not shutting down correctly
- out of battery during sleep
- blue screen
- lack of testing during managed application deployment
- lack of testing during firmware upgrade
- motherboard repair
- clear TPM chip
So the recovery password is a 48 digit password that is used to unlock your BitLocker encrypted drive when something is wrong with the TPM. The recovery password can be accessed at any time by a local administrator, by using PowerShell or manage-bde.exe. Look for RecoveryPassword or numerical password. The ID for the protector is a unique identifier for that encrypted drive.
The recovery password will never be changed or modified, but you can manually delete the protectors and add it again to create a new recovery password. Every time the password is disclosed to a user you should re-create the protectors to make sure that the recovery password will not be possible to use more than once. If you use Active Directory to backup your recovery information you need to develop a custom solution to delete and create the protectors to stay safe – else the encryption is useless is the recovery password information is in the wrong hands and never managed. Keep in mind that Active Directory backup is static! It will never update your recovery information, it will not audit who and when looks at the keys, it will not make sure your clients are compliant with the group policy settings you apply, it will not change your encryption algorism from AES128 to XTS-AES256 and so on.
As you probably already guessed MBAM will help you with all that. When service desk disclosed a password to a user MBAM agent it will automatically update the recovery password next time the client boots, it will make sure the client is compliant with settings etc.
Short note regarding Azure AD
So you are running cloud based clients? Nice to hear, but how is the BitLocker recovery information and TPM information handled there? Similar to Active Directory, BitLocker recovery information is saved to your Azure AD directory, or if you logon with your MSA/Live/Hotmail account it will be stored with that user information. Note this recovery information will not automatically be updated if the recovery password is disclosed.
What about TPM? Nothing, there are no automatic management of TPM owner password in a cloud managed way today. If you need this you need to develop a custom solution.
My recommendation
Every customer using Windows Enterprise I recommend to implement MBAM, Microsoft BitLocker Administration, to take care about both TPM owner password and BitLocker recovery information. When all in place it will make life simpler, MBAM will take care about many things that you have to develop custom solutions for such as replace BitLocker recovery key when disclosed, recovery key auditing, self service portal, group policy settings compliance, status reporting, compliance reports etc.
The high-level MBAM architecture consists of a SQL database and reporting services (Standard or Enterprise and TDE support), web services for service desk, self service and agent web service and a client agent. It can also be integrated into ConfigMgr. In most scenarios I recommend a two server implementation similar to the design below.
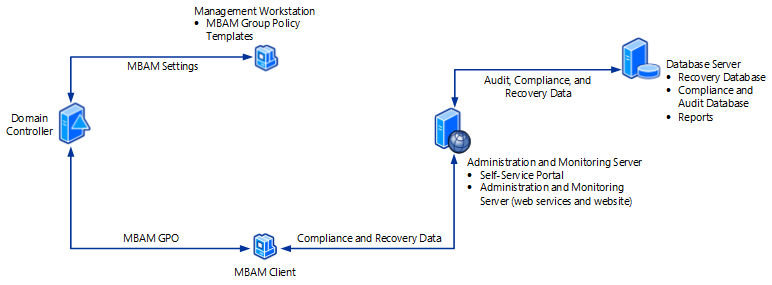
More information can be found on TechNet: https://docs.microsoft.com/en-us/microsoft-desktop-optimization-pack/mbam-v25/
Don’t forget testing and validation
When everything is in place, with or without MBAM make sure you test at least the following and document it
- Installation with a new machine (clear TPM and clear Bios settings to simulate this scenario)
- Reinstallation within Windows with TPM cleared and not
- Reinstallation from network/media with TPM cleared and not
- Recovery information from an encrypted hard drive
- Test application deployments with an extra reboot
- Test your TPM recovery password with Unblock-Tpm
- Verify BitLocker recovery password, use manage-bde –ForceRecovery
- Develop a way to communicate the recovery information to the user. Text, email, voice?
- How to handle hardware repairs
I haven’t talked anything regarding recommendations for Bios/Uefi firmware upgrades, but be sure to keep ’em updated. That will simplify your BitLocker implementation if you know your environment. Also automate your Bios/Uefi settings, there are soo many tools and scripts around today that will help you to configure Bios/Uefi
Did I miss any information or is anything unclear, ping me and I will do my best to fix it.
Post regarding how to implement TPM management and BitLocker pre-provision with MBAM in a ConfigMgr Task Sequence with and without MDT coming up.



Leave a comment